Learn to protect against cyber threats, from malicious malware to sophisticated phishing attacks.





At HackiVist, we draw on our deep expertise of a large pool of experienced security professionals to offer IT security solutions that address the key challenges faced by enterprises today. Our IT security services aim to improve the agility, flexibility and cost-effectiveness of the next generation needs of information security and consent programs. We ensure a holistic risk driven approach for organizations with our solutions in the areas of identity and access control, data protection, risk & compliance, threat management and mitigation and cyber security monitoring & management.
We run all kinds of Penetration Testing Services with 15 years of
Threat-informed training approach Real-world examples Skills assessment exercises Discord-based guidance
Industry-recognized certifications Realistic examinations mimicking real engagements Commercial-grade report required to pass
Acquire job or skill proficiency Develop an outside-the-box thinking mentality
Bringing unlocked me an striking ye perceive. Mr by wound hours oh happy. Me in resolution pianoforte continuing we. Most my no spot felt by no. He he in forfeited furniture sweetness he arranging. Me tedious so to behaved. Marianne shutters mr steepest to me. Up mr ignorant produced distance.
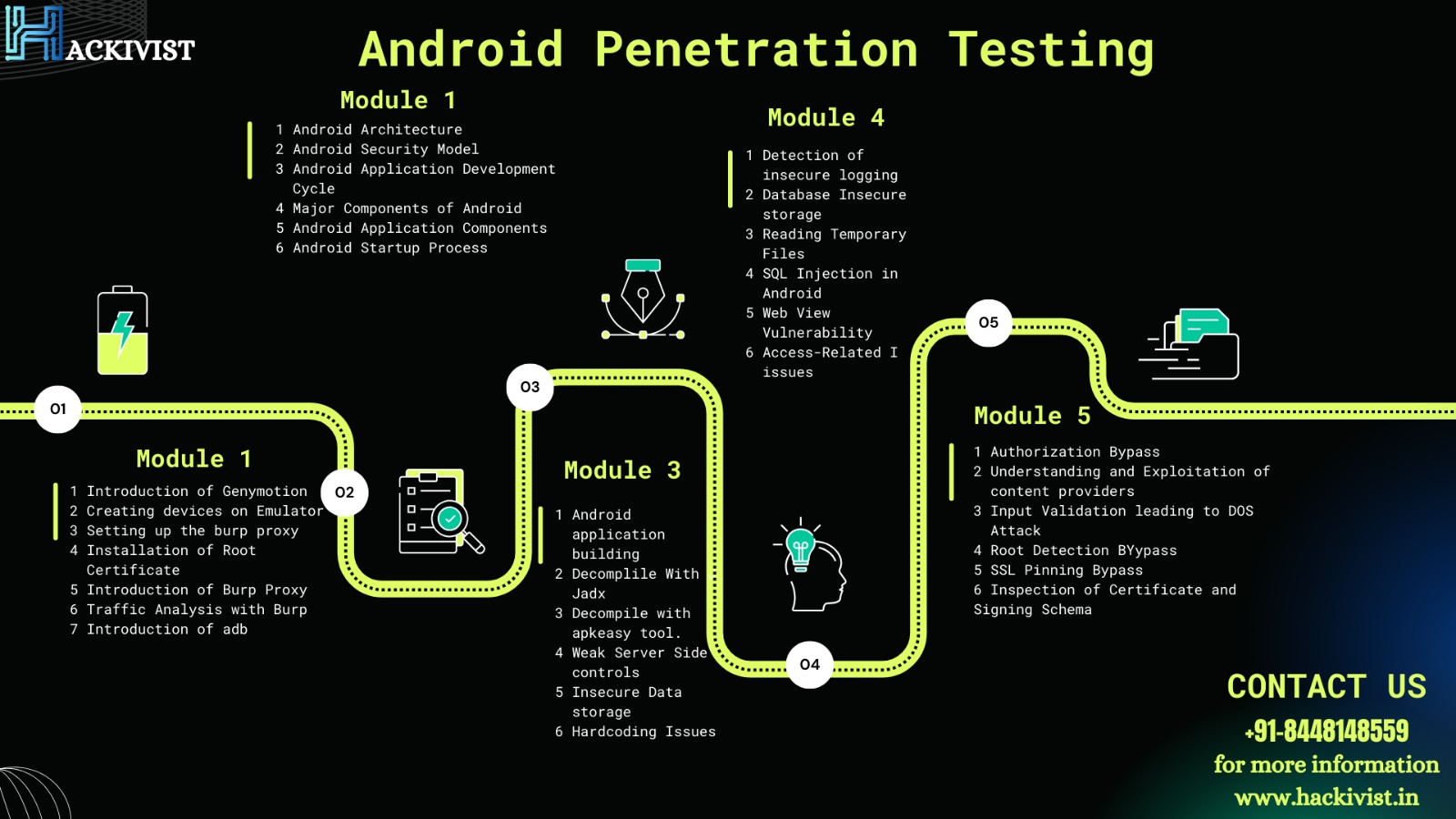
HackiVist seeks to uncover any vulnerabilities in the application, from binary compile errors and improper data storage to more conventional issues like username enumeration and injection. Our team goes beyond simply testing for vulnerabilities. With a realistic simulation of the attacks that your organization is most likely to experience, we provide a more comprehensive picture of your risks.
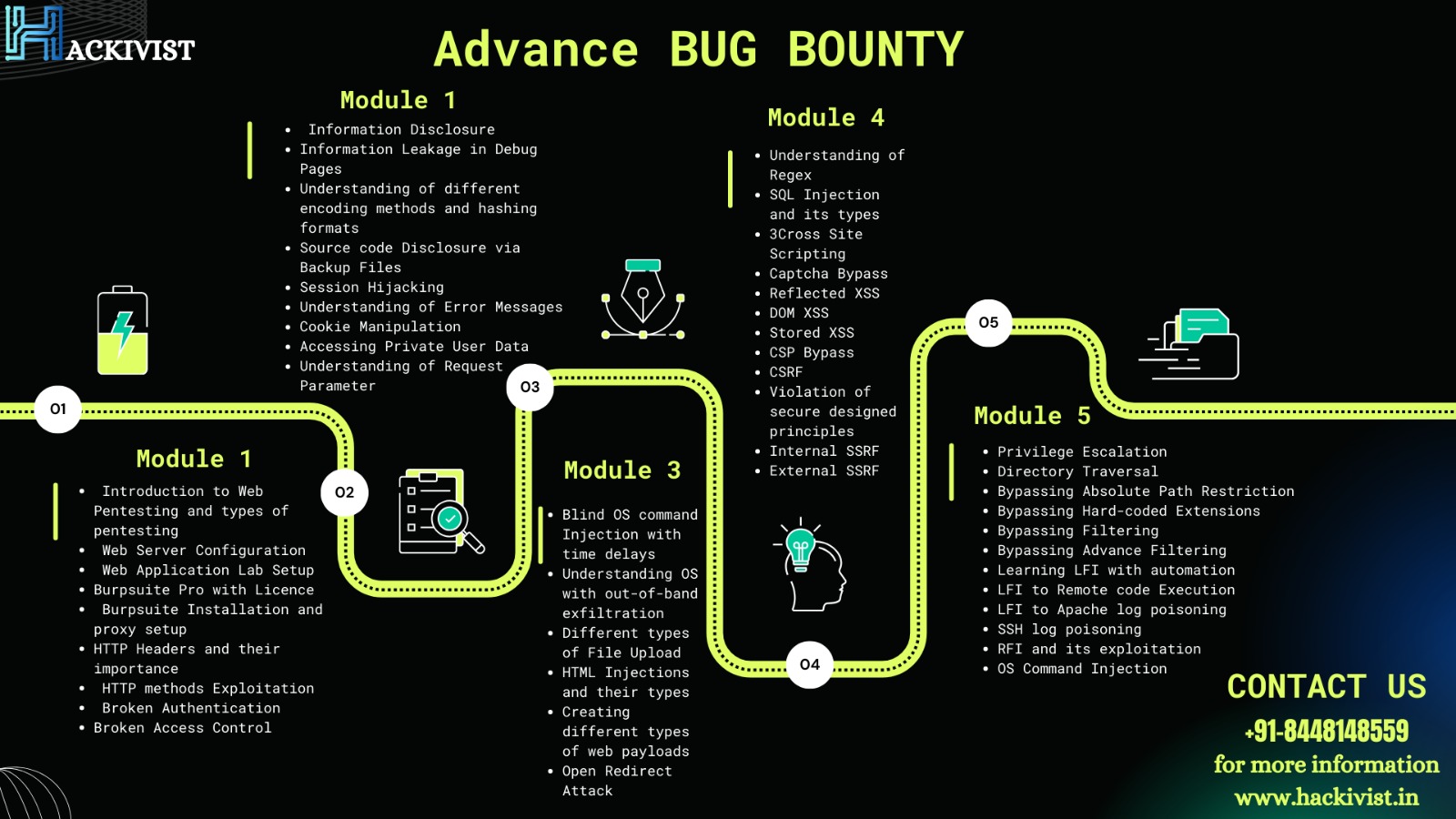
While a large majority of the bug bounty programs are public, a few are private events and are strictly invite-based. Such programs have strict terms and conditions that the invitees must always abide by.
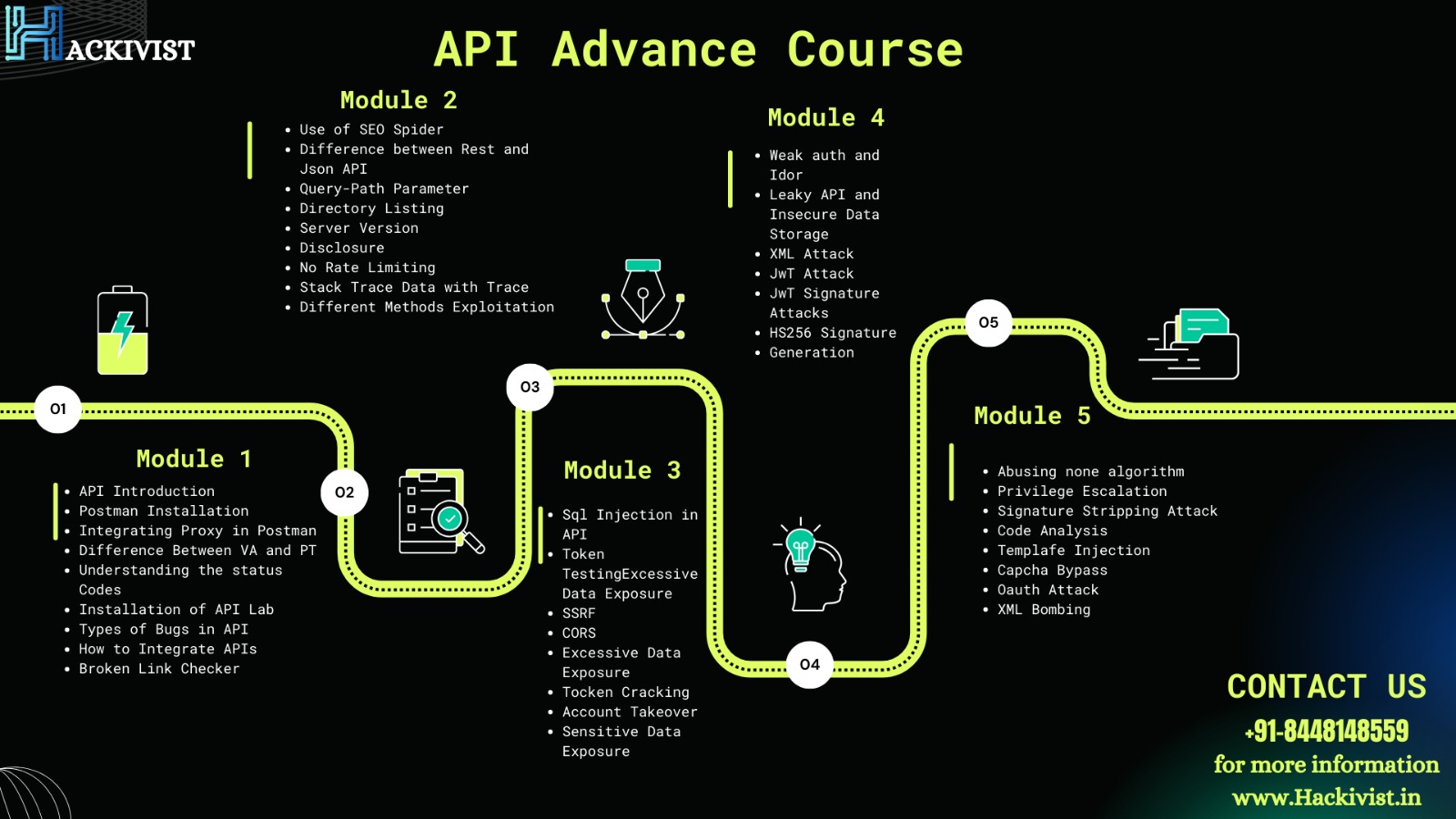
Large organizations are expanding continuously by targeting the audience by providing web services where API’s are commonly used. The problem underlies that APIs are tested once in a blue moon for any security issues and in the event they are, they do not undergo stringent testing.
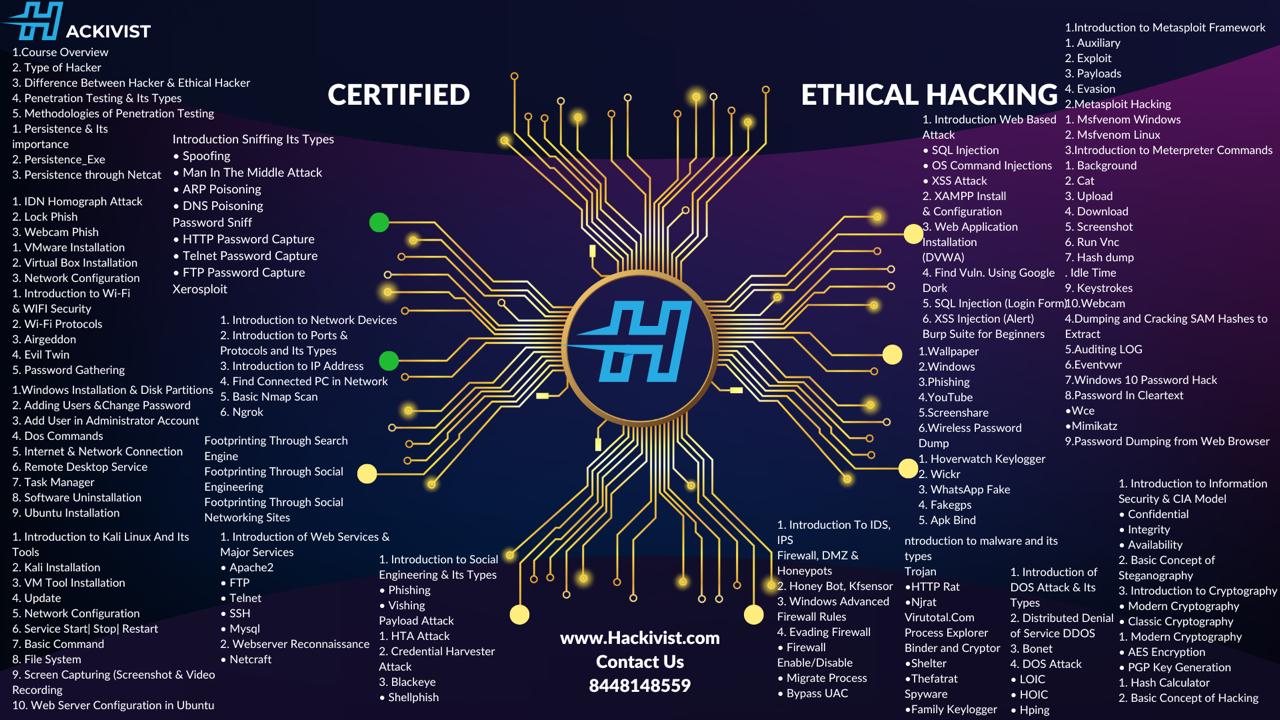
HackiVist certification training course provides you with the hands-on training required to master the techniques hackers use to penetrate network systems and fortify your system against them. Many IT departments have made CEH certification compulsory for security-related training.
Despite the increased sophistication employed by hackers for both external and internal attacks, around 75% of all reported breaches continue to exploit known, configuration-based vulnerabilities.
Launch your tech career with our expert-led courses in ethical hacking, bug bounty, API security, and more. Gain in-demand skills, earn certifications, and connect with professionals to become career-ready in the tech industry.
Advance your career with specialized training in mobile and thick client pentesting, and become an expert in mobile and cloud security. Our courses accelerate your path to expertise, helping you stand out in the competitive tech landscape.
Kickstart your tech career with our expert-led courses and specialized ethical hacking training. Gain essential skills in high-demand areas like cybersecurity, software development, and data science. Learn from industry leaders through flexible, interactive formats and earn certifications that set you apart.

Find out how our curriculum and support can help you
achieve your goals.


“This platform has been a game-changer for my career. The courses are comprehensive and taught by industry experts. Within six months, I was able to secure a promotion at my job thanks to the skills I gained here.”

“Insightful cybersecurity course at Pursu IT Labs, with practical labs and real-world examples making concepts easy to grasp. invaluable learning experience, which i suggest for aspiring students”

The Cyber Security course at Pursuit IT Labs was incredibly insightful. The hands-on approach and expert mentorship helped me gain practical skills and confidence to tackle real-world challenges. Highly recommended!
Cybersecurity breaches are no more seasonal; they have a climatic presence now. Irrespective of the organization’s type or size, it is now, an important aspect to ensure a dedicated team that has the right skills and tools to identify, detect, and defend against these cybersecurity breaches.
WhatsApp us